The Computer Emergency Response Team announced that multiple media websites in the Washington D.C. area were compromised with malware that was being served to the visitors of the website. The attackers used an exploit kit and embedded an iFrame into the websites that redirected the users to a hostile website that would download a version of the Zero Access Trojan onto their computer. The exploit kit has been identified as Fiesta exploit kit.
Cyber-Mafia Organizations, usually based out of Russian and Eastern Europe, engage in click-fraud against online advertising agencies. The problem with engaging in click-fraud is that online advertising agencies can detect that a specific click is coming from the same machine over and over. So in order to mask the fraud, criminals have to hijack other machines and automate the click fraud process. Malware is developed to carry out this process.
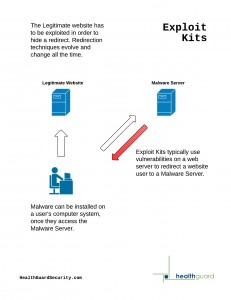
However, hijacking machines can be difficult. Software is developed to exploit vulnerabilities in people’s computers. They often pray on middleware applications like Java and Adobe. In order to get the exploit kit to install on a target machine, a wide variety of techniques can be used such as spam emails and compromising websites. The exploit kit allows the attack server to deliver the malware payload.
Exploit kits can be provided to cyber-criminals as a packaged software/hardware configuration, which creates an Exploits As A Service (ExAAS) business model. There are different types of business models between these organizations that allow for franchising and affiliate business partnerships. (F-Secure Report, 15)
Java has been a big target for exploit kits recently. Java was developed originally by Sun Microsystems in 1995 and was purchased by Oracle in 2009 and has continued its development.
Java is a very popular programming language because it allows developers to write one set of code and then distribute their application across multiple devices and operating systems. The device just needs to have Java Middleware installed and it can run the developer’s code. This has driven down development costs for many businesses.
However, many recent security problems have created a lot of bad publicity for the Oracle Corporation. Oracle is assuring their customers that they plan on taking security seriously and have released new security updates.
Resources:
The State Of Web Exploit Kits – HP
Zero Access Trojan Wikipedia Entry
WTPO Press Release On Cyber-Attack
Zero Access Trojan Removal Tips For Windows 7
Symantec’s Zero Access Trojan Page